Hyper-V Servers
Table of Contents
- 1 Hyper-V Servers
- 2 “Hyper-V Servers: Microsoft’s Virtualization Platform for Windows Servers”
- 3 what is Hyper-V server:
- 4 Hyper-V server installation and configuration:
- 5 Hyper-V Server is a standalone hypervisor-based server virtualization product from Microsoft that allows you to create and manage virtual machines on a single physical server. Here’s a step-by-step guide on how to install and configure Hyper-V Server:
- 6 Virtual machine networking in Hyper-V:
- 7 Here are some of the key aspects of virtual machine networking in Hyper-V
- 8 Storage options for Hyper-V virtual machines:
- 9 Hyper-V virtual machines require storage resources to store their virtual hard disks, snapshots, and configuration files. Here are some storage options for Hyper-V virtual machines:
- 10 Prevent your data loss
- 11 What is the data?
- 12 Impact of data loss on a website
- 13 Reasons of data loss in a website
- 14 Malware and Computer Viruses
- 15 Hacking the Website
- 16 System Error
- 17 Best Techniques to prevent data loss
- 18 Ransomware is a new threat to business
- 19 List of companies affected by ransomware
- 20 Plan B – Be prepared for worst case scenario
- 21 Data backup & restore with HostingRaja
- 22 Real time case studies of not having backup
- 23 List of backup & restore software
- 24 How many incremental backup is recommended (Frequency of backup)
- 25 What are the critical data needs to be taken as backup
“Hyper-V Servers: Microsoft’s Virtualization Platform for Windows Servers”
* Hyper-V enables efficient server consolidation by running multiple virtual machines on a single physical server. For more demanding needs, a Dedicated Server can be used, leading to cost savings and improved resource utilization.
* Hyper-V provides robust security features, including secure boot, shielded virtual machines, and host-based protection, to help protect against threats and safeguard sensitive data.
what is Hyper-V server:
1) Hyper-V Server is a standalone hypervisor-based server virtualization product from Microsoft. It is a free, bare-metal hypervisor that allows you to create and manage virtual machines on a single physical server.
2) Hyper-V Server is optimized for virtualization and is designed to provide a reliable and efficient platform for running virtual machines.Hyper-V Server includes a range of features that are designed to make it easy to create and manage virtual machines. These features include support for live migration, virtual networking, and the ability to create and manage virtual hard disks.
3) Hyper-V Server also includes tools for monitoring and managing the performance of virtual machines, as well as backup and recovery options.Hyper-V Server is a popular choice for virtualization in enterprise environments, particularly in organizations that already use Microsoft technologies such as Windows Server and System Center. It provides a reliable and efficient platform for running virtual machines, and it is designed to be easy to manage and maintain.
4) Overall, Hyper-V Server is a powerful and flexible hypervisor-based server virtualization product that allows you to create and manage virtual machines on a single physical server. It is a popular choice for virtualization in enterprise environments and provides a range of features and management tools that make it easy to use and maintain.
Hyper-V server installation and configuration:
Hyper-V Server is a standalone hypervisor-based server virtualization product from Microsoft that allows you to create and manage virtual machines on a single physical server. Here’s a step-by-step guide on how to install and configure Hyper-V Server:
1)Download Hyper-V Server: You can download the latest version of Hyper-V Server from the Microsoft website. It’s a free download, and you can choose the version that matches your server hardware.
2) Create a bootable USB drive: Once you have downloaded the Hyper-V Server ISO file, you need to create a bootable USB drive to install it. You can use tools like Rufus or the Windows USB/DVD Download Tool to create a bootable USB drive.
3) Install Hyper-V Server: Follow the on-screen instructions to install Hyper-V Server on your server. During the installation process, you’ll need to select the language, time zone, and other basic settings.
4) Configure networking: Once the installation is complete, you’ll need to configure the networking settings. Hyper-V Server supports both physical and virtual network adapters. You can use the Server Configuration tool or the PowerShell command line to configure the network settings.
5) Create virtual machines: Once the Hyper-V settings are configured, you can create virtual machines. You can use the Hyper-V Manager console to create virtual machines and configure their settings.
6) Install the operating system: Once the virtual machine settings are configured, you can install the operating system on the virtual machine. You can use an ISO file or a physical installation media to install the operating system.
7) Manage virtual machines: After the virtual machine is installed, you can manage it using the Hyper-V Manager console or PowerShell. You can start, stop, or modify the virtual machine settings as needed.
Virtual machine networking in Hyper-V:
Here are some of the key aspects of virtual machine networking in Hyper-V
1) Virtual Switches: A virtual switch is a software-based switch that enables virtual machines to communicate with each other and with the outside world. Hyper-V supports three types of virtual switches: external, internal, and private. An external virtual switch connects to a physical network adapter on the host computer, while an internal virtual switch allows virtual machines to communicate with each other and the host computer, but not with the outside world. A private virtual switch allows virtual machines to communicate with each other, but not with the host computer or the outside world.
2) Virtual Network Adapters: A virtual network adapter is a software-based network interface that is used by virtual machines to communicate with the virtual switch and the outside world. Hyper-V supports two types of virtual network adapters: synthetic and emulated. Synthetic network adapters provide better performance than emulated network adapters, but require integration services to be installed on the guest operating system. Emulated network adapters provide compatibility with legacy guest operating systems, but have lower performance than synthetic network adapters.
3) Network Isolation: Network isolation is a security feature that allows you to restrict network traffic between virtual machines and between virtual machines and the host computer. Hyper-V supports network isolation through VLAN tagging, which enables you to assign virtual machines to different VLANs and restrict network traffic accordingly.
4)Network Quality of Service (QoS): Network QoS is a feature that allows you to prioritize network traffic and allocate bandwidth to virtual machines based on their importance and resource requirements. Hyper-V supports network QoS through Quality of Service policies, which enable you to specify the minimum and maximum bandwidth for each virtual machine.
5) Virtual Machine Queue (VMQ): VMQ is a hardware-assisted networking feature that enables virtual machines to receive network packets directly from the network adapter, instead of going through the host computer. VMQ can improve network performance by reducing the overhead on the host computer.
Storage options for Hyper-V virtual machines:
Hyper-V virtual machines require storage resources to store their virtual hard disks, snapshots, and configuration files. Here are some storage options for Hyper-V virtual machines:
1) Virtual Hard Disks (VHDs):
Virtual Hard Disks (VHDs) are files that store the operating system, applications, and data of a virtual machine. They can be stored on physical disks or a storage area network (SAN) and are supported by Hyper-V in various types, including fixed-size, dynamically expanding, and differencing disks. VHDs are commonly used in virtual machines, and businesses seeking scalable storage solutions might consider using a VPS (Virtual Private Server), which offers flexible storage options tailored to diverse needs.
2) Pass-through Disks:
Pass-through disks are physical disks that are directly attached to a virtual machine. They provide direct access to the physical disk hardware, bypassing the virtualization layer. This can improve performance for certain workloads that require high I/O operations.
3) Cluster Shared Volumes (CSVs):
Cluster Shared Volumes (CSVs) are a feature in Hyper-V that allow multiple nodes in a cluster to access the same shared storage simultaneously. This enables virtual machines to move between nodes without requiring storage migration
4) Storage Spaces:
Storage Spaces is a technology in Windows Server that enables virtualization of storage by pooling physical disks into storage spaces. This provides features such as data redundancy, thin provisioning, and tiered storage. Storage Spaces can be used to store virtual hard disks for Hyper-V virtual machines.
Prevent your data loss
What is the data?
Data can be referred to as the structured and unstructured information which is in the form of files, documents and images. This is used by website owners and businesses on a daily basis. For a better insight and better decision making one can analyse data for its strategic moves.
Nowadays businesses are utilising, sharing as well as storing the information in different formats few of them are mentioned below:
- Email services and messaging
- Websites and blogs
- Different social media platforms
- Video and audio files
An individual should always remember to protect the data either if the business is big or small.
Impact of data loss on a website
Data loss can cause a major inconvenience to a website owner as it disrupts the working of a business. Whenever a data loss happens of important files and documents one has to spend the time and money for recreating and restoring the files. This can affect the business as a whole.
Loss of data makes the website, it can also make the website go offline, loss of clients and most importantly affect on the SEO rankings.
Reasons of data loss in a website
Losing the data can be the worst nightmare for any website owner who has worked on the website for months and years. Below are the few reasons why a website owner can lose the data:
Malware and Computer Viruses
Viruses and malware can slow the website or even make it offline completely. As a result the customers won’t be able to find the website over the internet. This will lose the customers as well as the revenue. Due to all these complications Hackers will be able to steal the client information.
Hacking the Website
Nowadays hacking has become more popular. Hackers can impact the business in a huge way which can damage the data by stealing as well as deleting the files. There is even a possibility that hackers can damage the whole network.
There is a possibility that people within the company or organisation can steal the information hence one should remember that we need to implement different levels of permission to the employees. This will help in the prevention of the data breach within the company.
Human Fault There is always a possibility of human error when it comes to data loss reports suggesting that the top reason for the website to go offline is due to human error. There are two types of human errors which usually result in data loss: one is by clicking the delete button or by formatting and the other probable reason is by damaging the storage device accidentally. Hence one must take care while getting rid of the files to the website or the business and the other important thing to notice is to store the hard drives and other hardware.
System Error
Sometimes you can lose the information because of system failure including electrical failures, controller failure and the servers going down because of the loss of data.
Best Techniques to prevent data loss
Frequent data backup – Frequent backups are essential, especially for WordPress sites. You can automate them using plugins or through hosting services that offer WordPress-specific backup solutions. This ensures an updated copy of all data is stored, typically on a separate disk or server, reducing the risk of data loss.
Enabling anti virus software – Installing and enabling an anti-virus and anti malware is essential in prevention of viruses and malware to protect the computer. Antivirus and anti malware must run properly and always keep it updated.
Ransomware is a new threat to business
What is Ransomware?
Ransomware can be termed as a malware which employs encryption to hold a victim’s information at ransom. Here the organization’s data is encrypted in a way that they will not be able to access the files, databases and the applications. A ransom is then demanded in providing the access. Here the ransom is then demanded to provide the access. A ransomware spreads quickly across the network and it targets the database and file servers. Cybercriminals are using ransomware to spread it across the organization and hence paralyzing the entire organization they are generating billions of dollars through Ransomware.
Ransomware is an attack which is carried out by the Trojan, it enters the system in multiple ways for example a malicious attachment, embedded link in the phishing email or a vulnerability in a network service. The program then runs the payloads which locks the system in a fashion or claims to lock the system by mentioning itself as a law enforcement agency and could claim that the system has been used in illegal activities such as pornography or a pirated media.
List of companies affected by ransomware
Thousands of businesses across the world have been affected by a ransomware attack centered on U.S. information technology on 2nd July 2021. Those who were attacked were Kaseya’s customers.
The top 5 UK ransomware attacks
NHS – In the year 2017, the NHS i.e. The UK’s National Health Service was affected for several days due to the WannaCry outbreak. This outbreak affected more than 200000 computers in more than 150 countries which resulted in the cancellation of thousands of operations and appointments. National Health services staff were also forced to come back to the pen and paper and they had to use their own mobiles after the key systems were affected which included phones.
Eurofins Scientific – UK’s biggest service provider of forensic and scientific services i.e. Eurofins was also affected by ransomware that caused disruption to the IT systems hence resulting in the backlog on more than 20,000 blood as well DNA samples.
Reckitt Benckiser – British pharmaceutical and CPG maker estimated that it had lost £107M pounds due to ransomware attack. Hence they were not able to deliver the goods to the customers and clean up the recovery costs.
British and Foreign Bible Society – This company was fined £100,000 by the Information Commissioner’s Office after the computer was attacked in the year 2016, this made the supporters’ payment card and the bank details at risk.
Police Federation of England & Wales – The police headquarters of England and Wales which represents more than 119 officers suffered a data breach which resulted from malware causing local servers and the networks which infected the deletion of the backup servers.
Plan B – Be prepared for worst case scenario
Trying to prevent data loss is one of the most important aspects that one must take care of. Companies need to be prepared for the worst case scenario which will ensure their data backup and recovery plan to face any challenges. Below are few typical worst case scenarios that one must be aware of:
Scenario 1:The main office succumbed to fire or gets destroyed by flood
A major flood can destroy the business and a tornado can make the building roofless. A major fire can gut the offices. If the data is stored in those places there is no way you can recover the vital information for running the business.
Backing up the data at a colocation or a Cloud Hosting will allow in restoring the business files even if the primary data center is destroyed.
One example of a fire breakout is given below
OVH Datacenter engulfed in Fire

Scenario 2: Long period of Outage
Imagine if the business experiences a long term outage mainly due to blackout or a natural disaster? Hurricanes can affect the power and damage the infrastructure which supports them which deprives the communities of the power for days and even for weeks. Even if the power is restored it might take time to recover the operations. Hence the business needs a secondary website so that it can be up and running quickly.
Data backup & restore with HostingRaja
Up till now you must have understood the real importance of taking a backup. Below are the few steps of taking a backup & restore in Plesk with HostingRaja.
- Step -1 You need to login to the Plesk panel and search for the domain name.
- Step -2 Click on the backup manager
- Step 3 – Click on the Backup
- Step 4 – To take backup of only the account settings, Select the “Domain configuration”.
For taking the backup of account settings and all the data of the customers subscriptions which includes database
select “Domain configuration” and “User files and databases”.
For taking only only the account settings and mail backup
Select “Domain configuration” and “Mail configuration and content”.
For taking complete account backup, select the option “Full” and Exclude log file (To improve the speed).
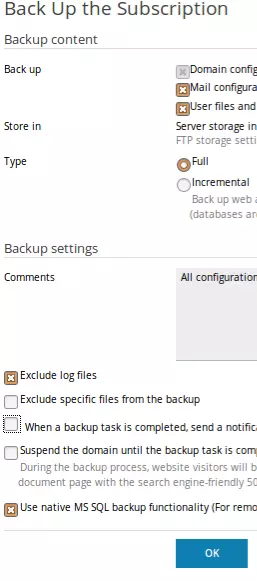
- Step 5 – Now click on OK
Now you can download the backup files once the backup is generated.
Below steps should be followed to Restore all data related to the account:
- Step 1 – Login Plesk Panel and search for the domain name.
- Step 2 – Click on the Backup Manager
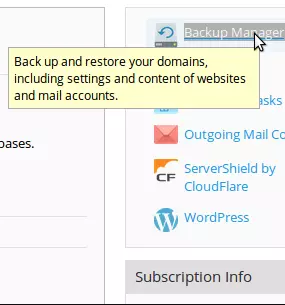
- Step 3 – Now you need to click on the Upload
- Step 4 – Click on browse files and select the backup files which need to be uploaded.
- Step 5 – You can select “Use password protection, if you have provided any password while downloading the backup file.
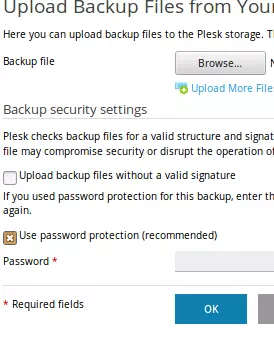
- Step 6 – Click on OK.
Real time case studies of not having backup
Data loss can affect the business in a huge way. There can be different factors associated for a data loss which includes weak password, phishing or equipment error. This disaster can happen to anyone at any point of time. Here we will give the real life scenarios on how important it is to have multiple data backups.
Amag Pharmaceuticals This pharmaceutical company hit a major setback when a folder related to HR activities was moved within the company’s Drive and hence it stopped syncing properly. This resulted in the files getting deleted. As a result the whole data was completely vanished.
U.K Prison U.K Prison system had a major setback in the year 2008 when an employee lost the USB which contained the personal information of the inmates such as name, age and release dates of over 80000 inmates. This disaster made the firm lose its major clients as well as huge revenue.
Dreamhost In the year 2007 Dreamhost had a major misfortune when 100’s of websites hosted by them disappeared from the internet. This major problem happened as a result of a bug in the routers. They tried to fix the problem but it was of no use, the DNS records of the clients were deleted by the bug. They were not able to restore the data of the clients and as a result they had to apologize to their customers for such a huge mistake. However, they have learnt from their mistakes and improved their security and stability.
List of backup & restore software
There are 100s of backup and restore softwares are available. We are going to discuss this from the hosting client’s perspective. As a hosting company, We provide custom backup & restore software built to suit our various needs.
- cPanel or linux shared hosting accounts come with account level backup.
- Plesk or Windows accounts come with account level backup
- Servers are taken as a whole server image backup using various softwares and custom scripts
How many incremental backup is recommended (Frequency of backup)
Generally It is recommended to have multiple backups in the event of disasters. You should have one weekly, one monthly and one daily backup. This is the most recommended backup frequency for all mid and small size companies.
What are the critical data needs to be taken as backup
Database or ecommerce transaction details need to be backed up once in a few hours. In some cases, the whole transactions are duplicated or mirrored in slave database servers. Emails backup can be taken once in a few hours or daily.
-

Dhanasekar Mani
Founder Of HostingRajaDhanasekar Mani, a seasoned SEO Specialist and Entrepreneur, brings over 23 years of expertise in software development. As the esteemed founder of HostingRaja and Webbazaar, he has played a pivotal role in shaping these ventures. He contributed to pioneering patented technologies, solidifying his impactful presence in the tech industry.
